This first post on smart buildings focuses on cyber security attacks that disrupt the normal function of a system, such as denial of service, radio signal jamming and electromagnetic pulse (EMP).
To provide some context for the discussion, smart buildings are defined as buildings that use technology and processes to effectively control their environment. This is accomplished through the use of IT-aided sensors and controls that allow for better building management and maintenance [1]. For those concerned with cyber security, awareness and understanding of potential attacks—even in smart buildings—are critical to developing effective defenses and recovery techniques. Using the ostrich algorithm [2] to deal with cyber security threats is no longer an option.
The current power industry evolution will take a generation to complete and will combine several well-established, yet distinct, industries. To deal with this consolidation, the U.S. Energy Independence and Security Act of 2007 appointed the U.S. Department of Commerce’s National Institute of Standards and Technology (NIST) to lead the development of interoperability standards. NIST has generated many important documents in recent years, especially the Guidelines for Smart Grid Cyber Security, that prohibit cyber security measures from interfering with safe and reliable power system operations [3]. This prohibition against power system interference provides an important context from which to evaluate disruptive cyber security attacks that deny service, jam radio signals or deal with electromagnetic pulse.
DENIAL OF SERVICE
Denial of service (DoS) is a type of cyber-attack that undermines the normal use of communication facilities [4]. DoS attacks can be very effective and difficult to detect, though defense techniques do exist. Here, we will look at one type of DoS attack called, “SYN Flooding” [5].
Establishing a TCP connection on a network starts with a "three-way handshaking" exchange. First, a client sends a connection requests (SYN) to the server that then replies with an acknowledgment (SYN+ACK). Finally, the client returns an ACK and the connection is complete.
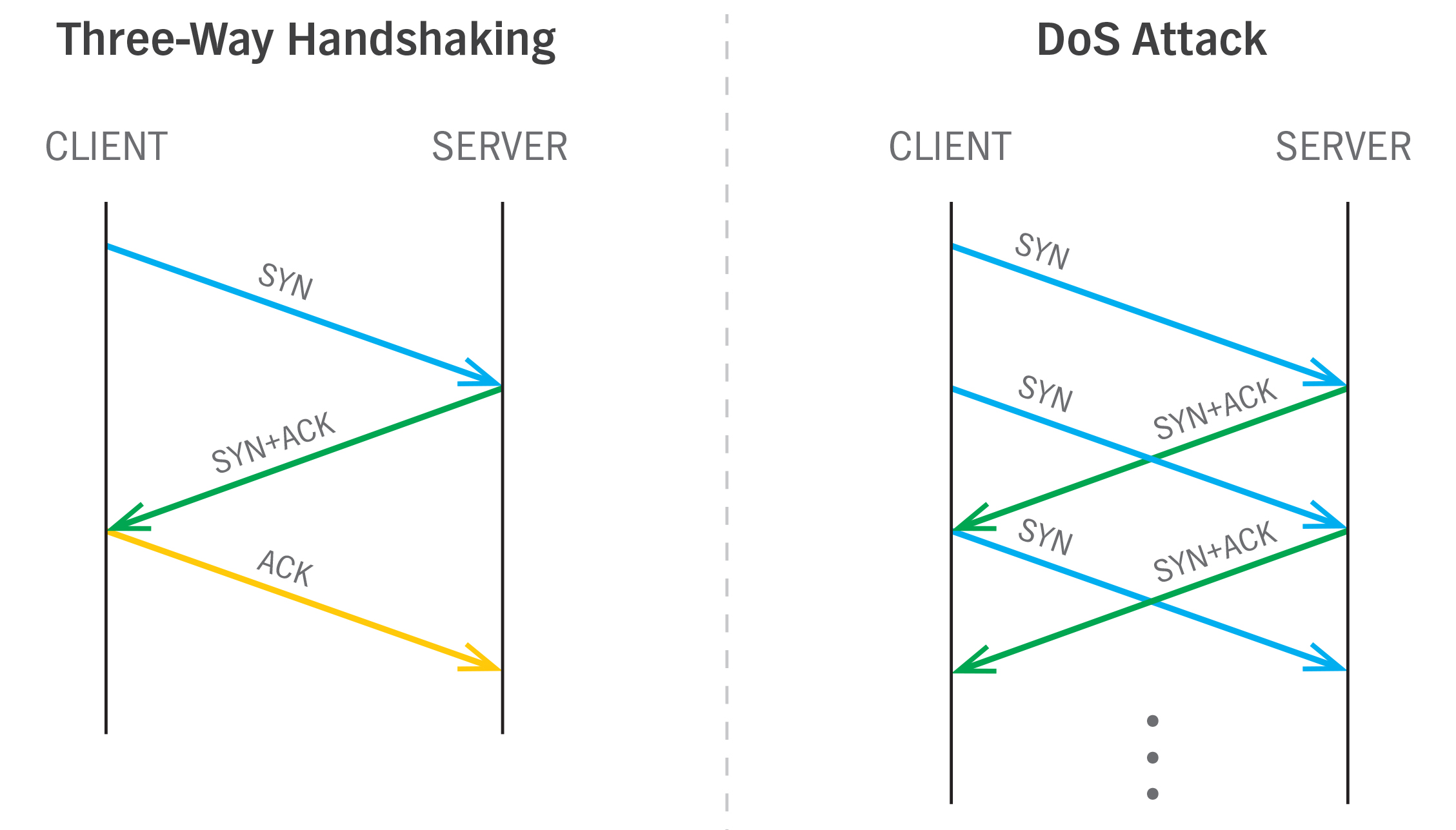
The server uses time and resources to handle every SYN request [6]. A DoS attack takes advantage of this time/resource element by only sending SYN requests. The handshaking is never meant to be completed. Instead, when several computers are sending SYN requests, the server spends all of its time and resources dealing with these bogus requests, which prevent it from effectively handling legitimate ones [5].
On a large-scale, this is called a distributed denial of service attack (DDoS). This attack can be carried out by a botnet, or a large collection of compromised computers under the control of a botmaster. In the past, these compromised machines were called “zombies” [7].
SIGNAL JAMMING
Signal jamming is the deliberate use of radio noise to disrupt wireless communications [8]. This can be applied to cellphones, Wi-Fi, Bluetooth or ZigBee—basically, any sort of radio communication. It isn’t very elegant, but can be used in very clever ways. In most countries, this practice (as well as the sale or manufacture of these devices) is illegal. In the U.S., signal jamming is covered by the Communications Act of 1934, which can subject an instigator to fines and imprisonment [9]. Even so, these devices can be easily purchased on the Internet and are fairly are inexpensive [10], or can even be built with off-the-shelf hardware.
Besides jamming phones or wireless lighting control systems, signal jamming has been used to jam GPS navigation systems [11] and car key fobs [12]. If such an attack occurs on a smart building, the question that needs to be addressed is: are there fail-safes in place to maintain human safety?
ELECTROMAGNETIC PULSE
Electromagnetic pulse (EMP) attacks have been much storied in popular fiction for decades, but they do exist and are part of a troubling trend. An EMP is a short burst of electromagnetic energy. Naturally-occurring types of EMPs include solar flares and lightning strikes. Man-made types come from nuclear explosions and brush contacts in electric motors [13].
In a recent IEEE article [14], researchers built a small EMP device using not much more than a generator, a car battery, and an antenna. In tests, the device was able to cause significant disruptions. As technologies have improved and become cheaper, while infrastructure has become increasingly dependent on "closely integrated, high-speed electronic systems operating at low internal voltages,” everyday items can be used to bring down systems with sharp high voltage pulses that are actually low on energy. Such an attack could be launched wirelessly or via a hard connection. The pulses have the effect of inducing a current in the internal wiring of electronics to disrupt and even physically damage them [14].
One defense against a wireless EMP attack is to surround all sensitive equipment with metallic wallboards, but there are practical concerns with such an approach. What is the likelihood of such an attack and what is the cost?
CONCLUSION
"If the cost of security is less than the likely cost of losses due to lack of security, security wins. If the cost of security is more than the likely cost of losses, accept losses” [15]. Much of addressing security issues in smart buildings and other systems will comes down to economics and a simple cost-benefit analysis. Yet, as we consider NIST requirements for safely-operating power systems, we need to focus on an effective means to recognize attacks, recover from them, and initiate a shut-down in the event of a failure, without threat to human safety. Computers systems are playing increasingly important roles in our daily lives and the time to recognize and plan for cyber security issues is now.
REFERENCES
[2] https://en.wikipedia.org/wiki/Ostrich_algorithm
[3] NIST 7628 Revision 1, “Guidelines for Smart Grid Cyber Security, Volume 1 – Smart Grid Cybersecurity Strategy, Architecture, and High-Level Requirements”, p. 5, September 2014.
[4] William Stallings, Cryptography and Network Security, p.8, Prentice Hall, 1999.
[5] https://en.wikipedia.org/wiki/Denial-of-service_attack
[6] Mahbub Hassan, High Performance TCP/IP Networking, p. 18, Prentice Hall, 2004.
[7] Mark Stamp, Information Security Principles and Practices, p.433, Wiley, 2011.
[8] https://en.wikipedia.org/wiki/Radio_jamming
[9] http://electronics.howstuffworks.com/cell-phone-jammer5.htm
[10] https://www.schneier.com/blog/archives/2007/10/cheap_cell_phon.html]
[12] http://www.theregister.co.uk/2010/09/21/car_jammer_vehicle_theft_scam/
[13] https://en.wikipedia.org/wiki/Electromagnetic_pulse
[14] http://spectrum.ieee.org/aerospace/military/electromagnetic-warfare-is-here
[15] Bruce Schneier, Data and Goliath, p. 142, W.W. Norton & Company, 2015.

